On Monday 11th March, I attended IEEE PerCom in Kyoto, Japan. PerCom is regarded as a top scholarly venue in the areas of pervasive computing and communications. It is my third year participating in this conference. This year, I presented a paper titled: “IoTSM: An End-to-end Security Model for IoT Ecosystems”, in PerLS’19 – Third International Workshop on Pervasive Smart Living Spaces.

My presentation, live demos, and paper awards at the International Conference Center in Kyoto (2019).
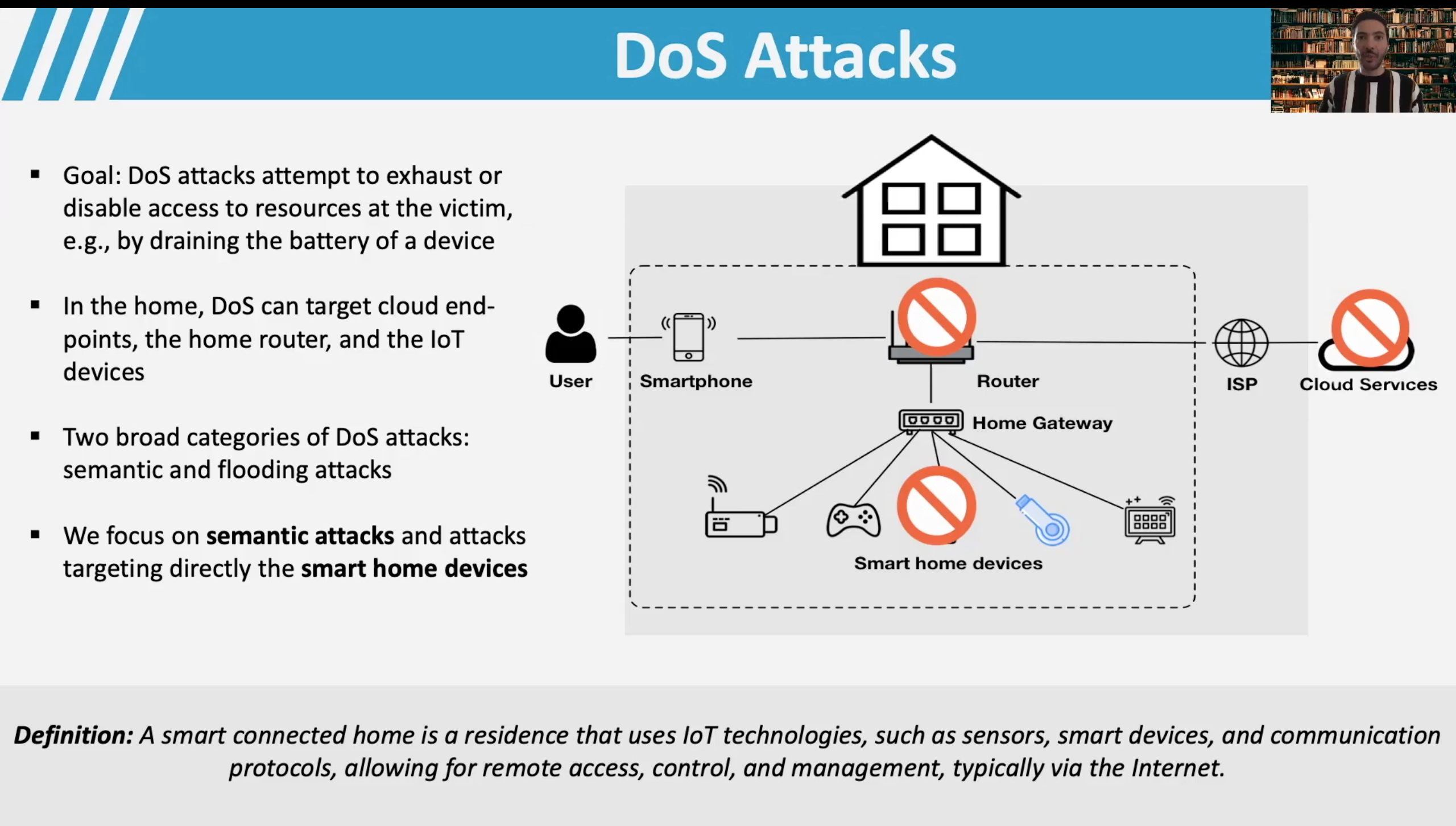
In my presentation, I talked about how most of the reviewed security frameworks and maturity models, tend to focus more on securing web applications and services, but have not evolved particularly to cater for the additional complexities and challenges that IoT technologies bring to the table. While most of the security practices remain similar, IoT requires additional checks and balances to implement effective security. Some reasons for this, is that IoT applications by their nature tend to be Internet-connected, deal with highly personal data, and feature complex interdependencies involving multiple stakeholders and third-party systems.
Reviewing the existing scholarly literature and interviewing various IoT security experts based in Sweden, we especially observe the need for continuous processes rather periodical processes. For instance, when it comes to risk assessment in IoT it is especially preferred if it is “continuous” in order to deal with the highly dynamic nature of IoT systems. Unfortunately, there is a shortage of methodologies for that and most of the related research work is still in its early stages. Moreover, we note the lack of security awareness common across the industry, e.g., with regards to “threat modelling”, but as well its applications to model data flows, in particular to deal with information privacy. Finally, we recognise the diversity of IoT security requirements. While for a traditional application, one needs to ensure service, network, and physical security for IoT one might need as well other to consider other requirements, e.g., that of ensuring resilience, data security, cloud security. Likewise, IoT may require to cater for additional threat agent goals. Such goals may not necessarily be related to confidentiality, integrity, and availability.
Take a look at my presentation: IoTSM: An End-to-end Security Model for IoT Ecosystems