Security and Academic Advisory Services
Cyber security services
- Security education: Learn how to protect coworkers, family, and friends with posters, newsletters, and in-house interactive sessions
- Policy development: Write master policy and specific policies for organisations

- Risk assessment: Conduct qualitative assessments identifying pertinent risk scenarios and proposing actionable mitigations
- Threat modelling: Provide threat models to identify threats to the software and weaknesses within designs and architectures
- Attacker modelling: Identify information security threat agents and most common attack scenarios
- Vulnerability management: Assess the security and safety of buildings, offices, and homes for the latest threats
- Penetration testing: Explore if vulnerabilities to resources can be exploited by malicious threat agents or prying eyes
- Security consultancy: Helping implement the best possible security solutions within a specified budget and requirements
Academic services
- Proofreading, editing, and rewriting of text for academic papers, research proposals, or technical reports
- Writing professional research-based cyber security blogs and articles covering topics such as the latest cyber threats, security best practices, or case studies
- Planning, organizing, and delivering training and education sessions on cyber security fundamentals, advanced concepts, or specialized topics like ethical hacking or digital forensics
- Coaching, mentoring, and providing academic support to students pursuing degrees or certifications in cybersecurity, helping with coursework, projects, and exam preparation
- Book writing services that focus on producing educational materials or textbooks related to cyber security, data privacy, responsible AI, and other topics
Security education and training services
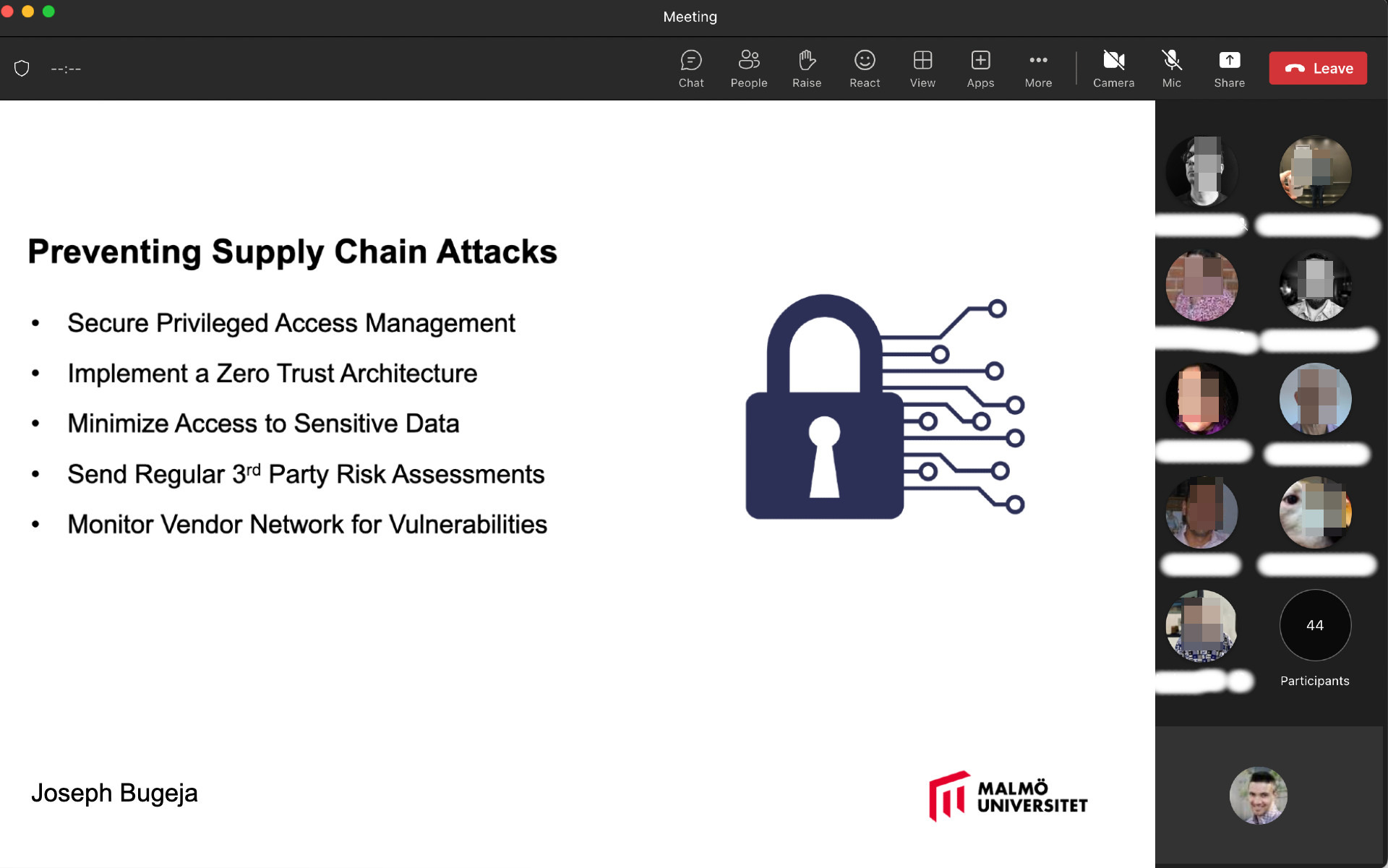
Televised sessions:
Focused sessions:

In-class sessions:


Online lectures and webinars:


Animated presentations:
Poster presentations:
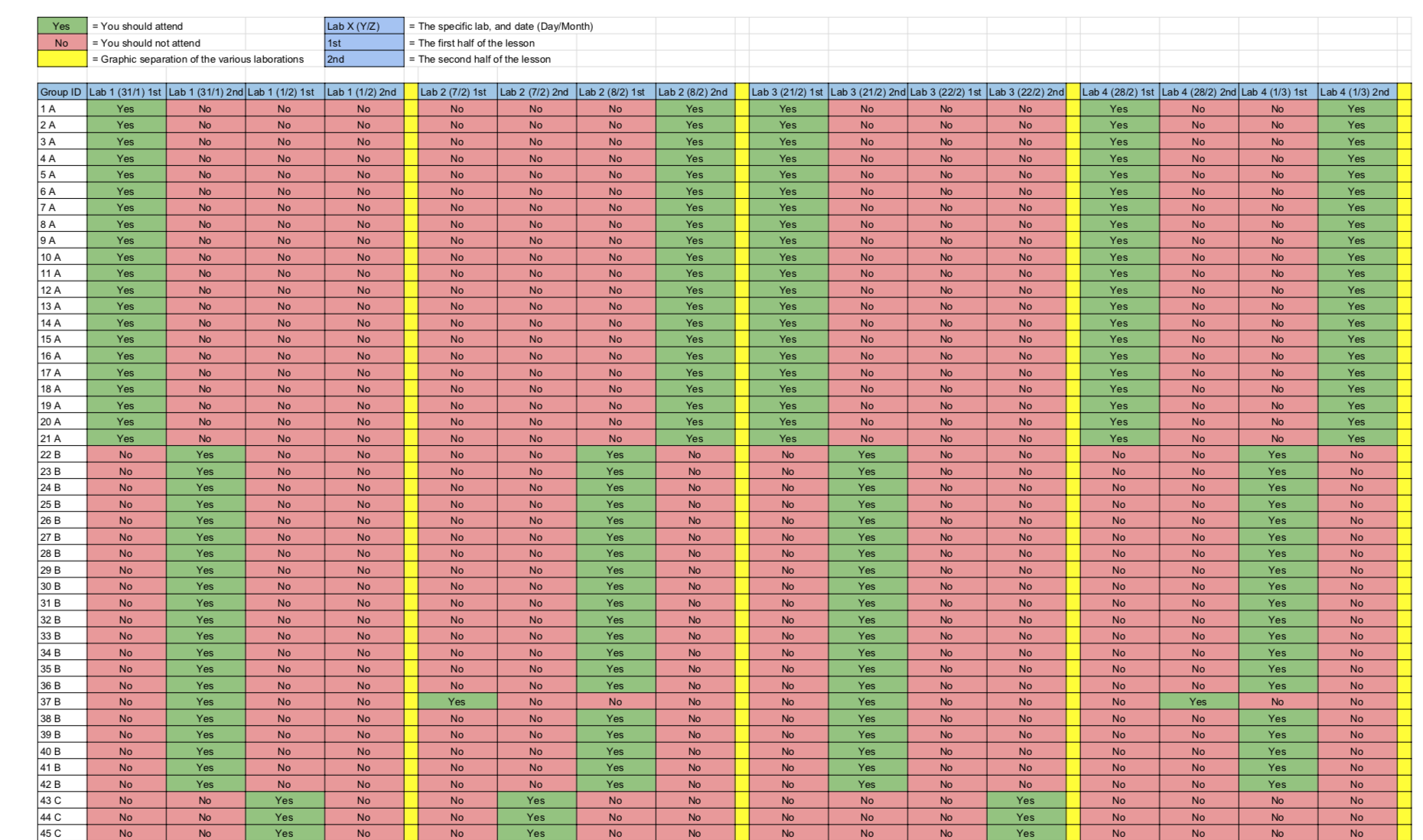
Lab session planning:
Online lab support:
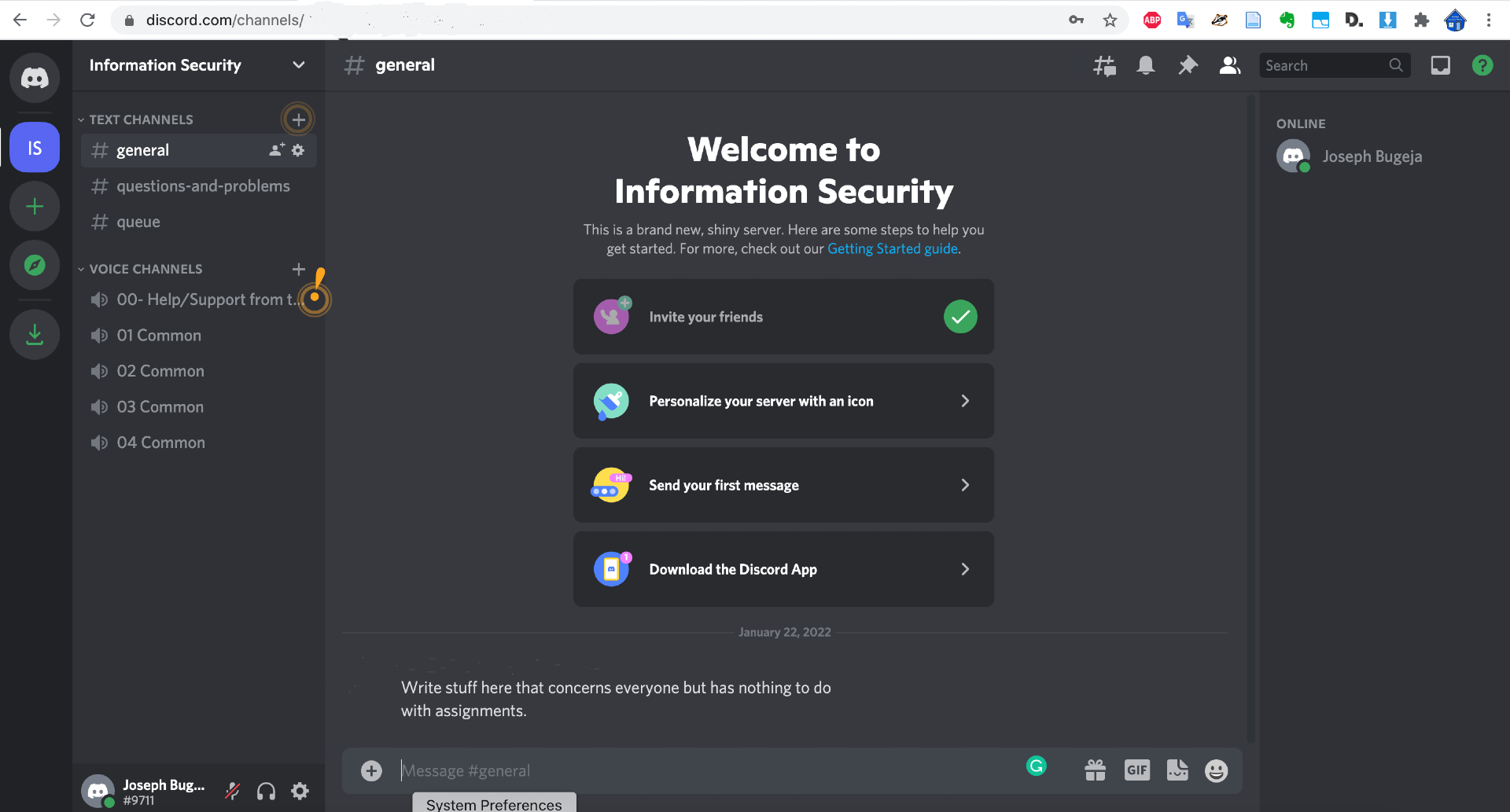
Course management:
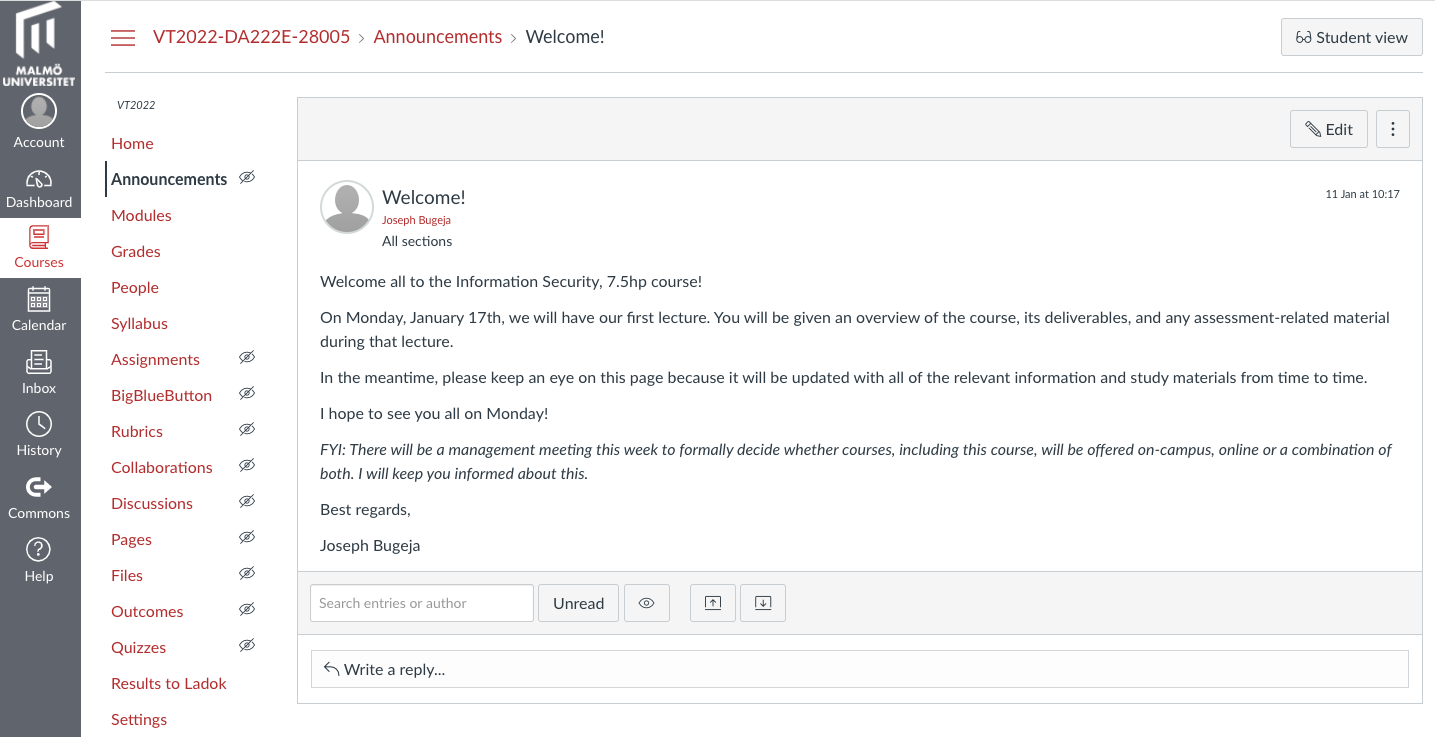
Sample lecture content:
- Topic: Access control fundamentals (redacted content based on Computer Security textbook and accompanying slides by Dieter Gollmann).
- Topic: Cryptography Primer (redacted content based on Computer Security: Principles and Practice textbook and accompanying slides by William Stallings and Lawrie Brown).
- Topic: Risk Analysis Foundations (redacted content based on CISSP All-in-One Exam Guide, by Shon Harris and Fernando Maymi).
Top 10 checklists for securing digital devices:
- Top 10 Tips for Securing Your Apple iPhone
- Top 10 Tips for Securing Your Android Phone
- Top 10 Tips for Securing Your Mac
- Top 10 Tips for Securing Your Windows Computer
- Top 10 Tips for Securing Your Docker Containers
- Top 10 Tips for Securing Your Amazon Alexa Devices
- Top 10 Tips for Securing Your Google Home Devices